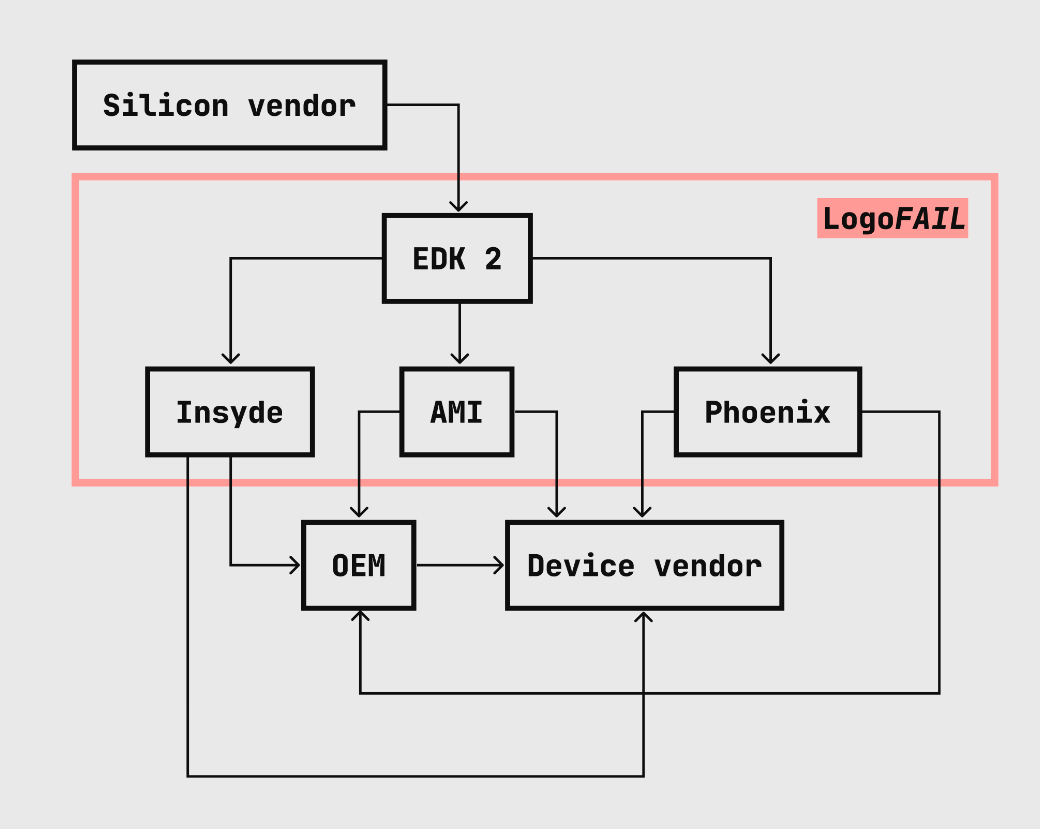
Lenovo, AMI and Insyde have launched patches for LogoFAIL, a picture library poisoning assault.
Researchers at firmware provide chain safety platform firm Binarly found a set of safety vulnerabilities that open virtually all Home windows and Linux computer systems as much as assault. The safety researchers named the assault LogoFAIL due to its origins in picture parsing libraries. Binarly introduced its discovery on Nov. 29 and held a coordinated mass disclosure on the Black Hat Safety Convention in London on Dec. 6.
Any x86 or ARM-based gadget utilizing the Unified Extensible Firmware Interfaces firmware ecosystem may probably be open to the LogoFAIL assault. Binarly continues to be investigating whether or not further producers are affected. LogoFAIL is especially harmful as a result of it may be remotely executed in methods many endpoint safety merchandise can’t detect.
This vulnerability will not be identified to have been exploited, although a number of distributors have launched patches.
Leap to:
How does the LogoFAIL assault work?
LogoFAIL is a collection of vulnerabilities whereby the graphic picture parsers in system firmware can use personalized variations of picture parsing libraries. Basically, an attacker can change a picture or emblem (thus the identify) that seems whereas the gadget boots up and acquire entry to the working system and reminiscence from there (Determine A).
Determine A
Assaults primarily based on the UEFI system firmware have been round for the reason that early 2000s, however “… the variety of picture parsers have considerably elevated through the years,” Binarly wrote. Extra picture parsers means a wider assault floor.
Put merely, attackers may embed malicious code into logos that seem throughout the Driver Execution Atmosphere stage within the boot course of, such because the gadget producer’s emblem. From there, attackers can entry and management the gadget’s reminiscence and disk (Determine B). Binarly has a technical clarification.
Determine B
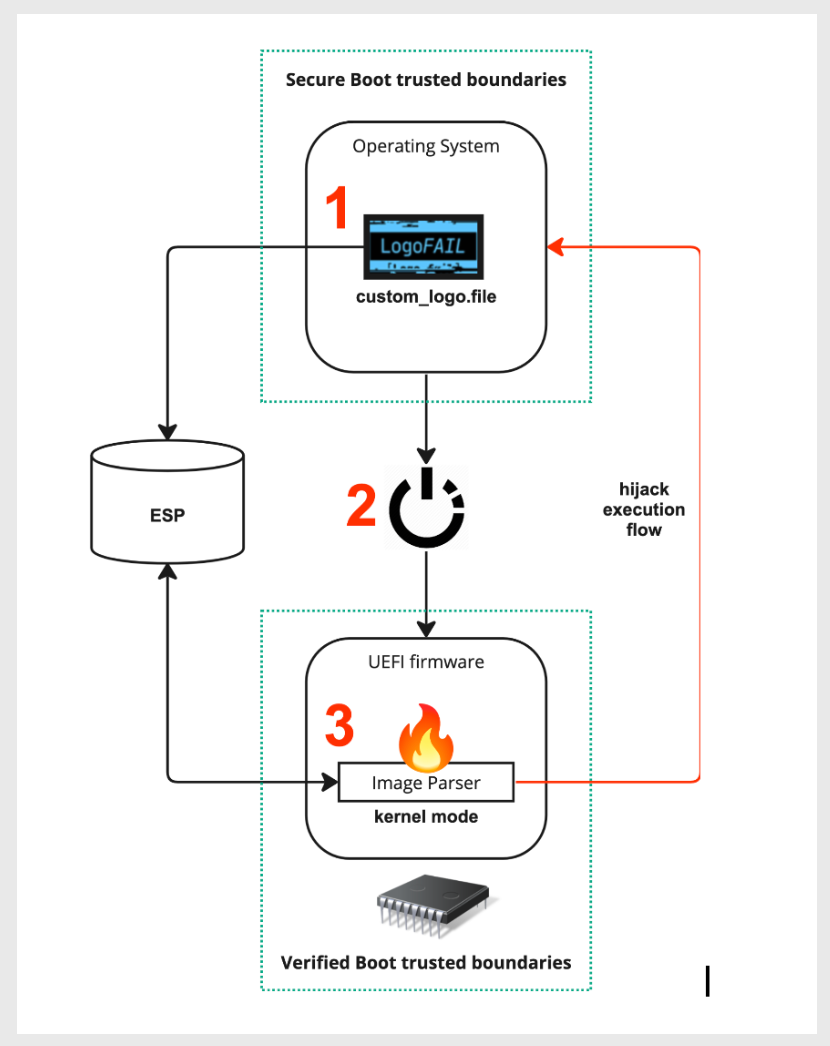
Binarly confirmed they may load executable code onto the onerous drive earlier than the gadget had totally booted up.
“Now we have been closely targeted on reporting vulnerabilities primarily found by the Binarly Transparency Platform product, however the work on LogoFAIL was totally different and initially initiated as a small analysis venture only for enjoyable,” Binarly’s group wrote. “After demonstrating an enormous variety of fascinating assault surfaces from image-parsing firmware elements, the venture grew into an enormous industry-wide disclosure.”
SEE: Cisco Talos analyzed cybersecurity tendencies of 2023 (TechRepublic)
The way to defend towards LogoFAIL
The next corporations have launched patches for LogoFAIL:
ArsTechnica recommends operating UEFI defenses reminiscent of Safe Boot, Intel Boot Guard, Intel BIOS Guard or their equivalents for AMD or ARM CPUs. Tech division leaders ought to inform workers how one can obtain patches as applicable.

